📬 Mailbag: Where should security communications be on the organization chart?
Mailbag questions are submitted anonymously by our readers. Submit your own question for our team at discernibleinc.com/blog.
The two most common options are inside corporate communications or the security organization. Although a lot of great security communications work can be done anywhere in the org chart, centralized oversight is important. When I worked in-house, I managed security communications from within the corporate communications department. There are two critical reasons for this:
Authority – Corporate communications professionals are usually authorized to speak on behalf of the company and have executive veto power (either through formal or informal influence) over a lot of external communications created by other teams. This can be a frustrating reality for a lot of security communications professionals who don’t report to this function.
Visibility – In addition to their experience managing external perceptions, corporate communications teams typically have more visibility into activities across the company, compared to security communications professionals within the security organization. Knowing what else is on the horizon for the business (or lurking in the shadows) provides a strategic advantage.
That said, my role was always created at the behest of the CISO/CSO and in collaboration with the head of corporate communications to ensure I had access to the advantages above. My first responsibility was to the company at large, and I knew the best way to do that was to ensure security communications were proactive and worked to prevent or anticipate issues, rather than simply react to them.
A depressingly large number of corporate communications teams are only concerned with media engagements, ignoring all other stakeholders. This is a disservice to themselves and their organization, which needs a responsible steward of the corporate brand across audiences. As explained by the Page Society (the world’s leading professional association for senior strategic communication leaders), a company’s brand isn’t just its product:
“It’s the totality of what is experienced by all stakeholders through every touchpoint.” – Page Society
A limited scope of corporate communications–or public relations more generally–as solely a publicity role is a waste of potential influence, power, and effectiveness for the function! Unless your business sells to newsrooms, media is primarily a communication channel, not an audience. You may not always be able to choose the topic or timing (freedom of the press is important!), but the reason organizations invest in these relationships is because of their potential to influence stakeholder groups that can impact their business.
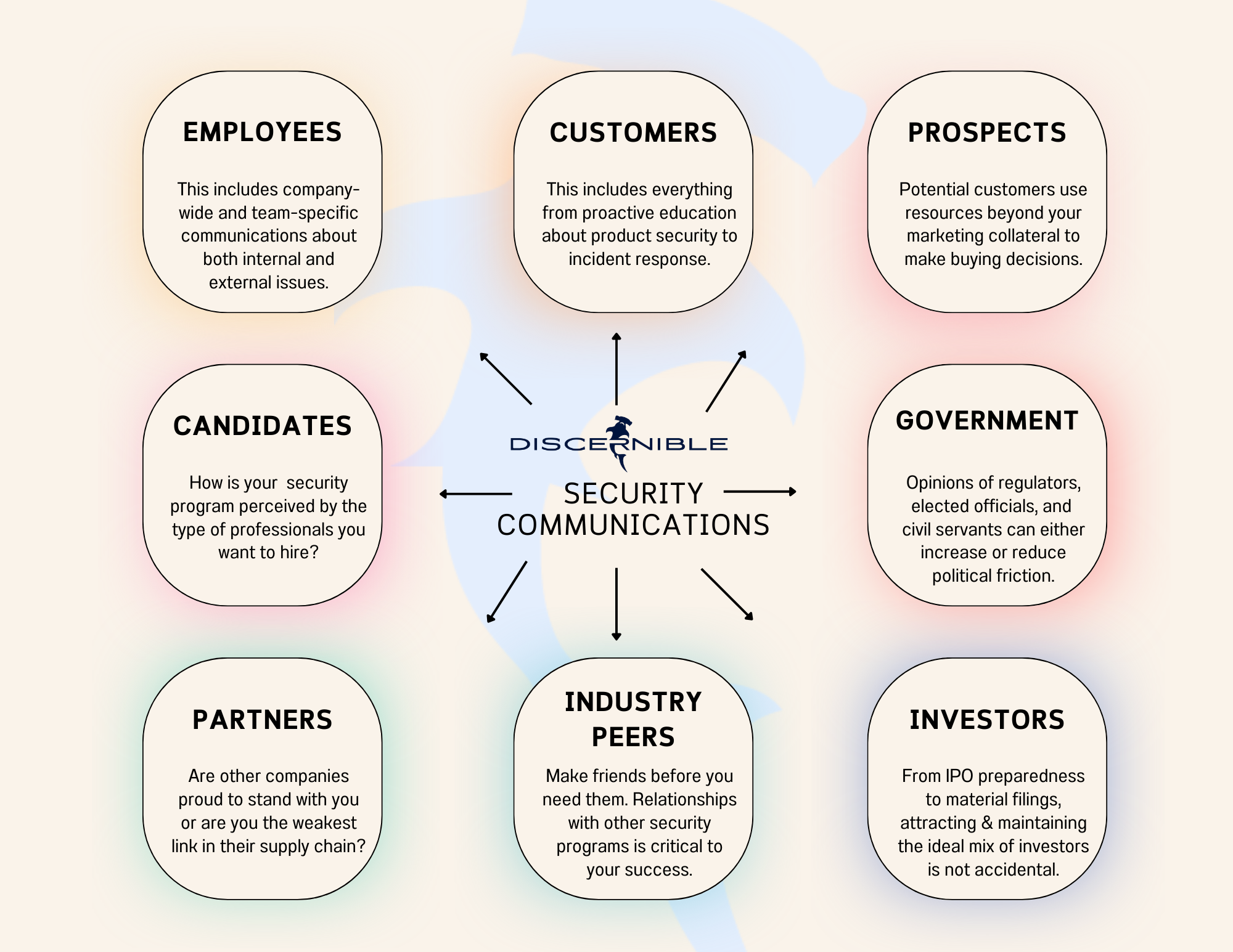
An ideal security communications function aligns communications across all stakeholder groups, considering the needs and expectations of each one as it relates to cybersecurity. At best, misalignment across audiences is a missed opportunity to strengthen and amplify your security reputation through repetition and message enforcement; at worst, misalignment creates conflicting or incomplete messages.
The Scope of Strategic Security Communications
Because of the multitude of audiences in scope for security communications, we’ve seen aspects of this work in a variety of places inside organizations. Unfortunately, they’re usually isolated and not aligned with any particular high-level business goal that the company is measuring. This leads to a lot of work that exists only for its own sake; and although you might be busy, there’s not much impact. When teams and individuals measure outputs instead of outcomes, it’s usually because they lack the visibility to connect with priorities from across the entire organization.
Names and titles within organizations vary, so the exact role or team might be different at your company, but here are some of the folks we work with most often to ensure accurate, consistent, and timely security communications:
Security: Including the CISO, their Chief of Staff, training staff, GRC/Assurance (especially what they share publicly & through procurement portals), incident response (external comms reflect the level of internal chaos), bug bounty teams (an often overlooked but very public-facing program), and individual team members to ensure everyone knows what’s expected of them in regards to building relationships and influence across the organization and the outside community – and have the communication skills to meet those expectations. It’s useful to sit in on security reviews for new products or engineering projects, and ask questions that will help teams think critically about the public perceptions of their decisions.
Corporate Communications: Internal/employee communications, investor relations, and product PR all intersect with security communications, but they usually don’t see it themselves until something bad happens and suddenly they’re asking for reactive talking points to address inbound questions. These are incredibly valuable colleagues to collaborate with in advance, to educate critical audiences while setting realistic expectations. For example, when you launch a new product or feature, consider how you will communicate security choices made on the backend or within the user experience to increase or protect current levels of security. Get ahead of anticipated concerns while demonstrating transparency and technical competence.
Trust & Safety: Fake or compromised accounts are involved in a lot of online abuse, and external audiences rarely differentiate your safety brand from your security brand. To them, it’s all connected to how safe they feel using your products. How you communicate about cybersecurity issues to people who use your products impacts their overall perception of brand and product safety. Your organization may not have this exact team; perhaps for your company, the function is more along the lines of platform integrity, anti-fraud, or spam fighting.
LERT: Collaboration with law enforcement agencies is increasing across a wider range of security incidents, in part because more and more attacks are cross-platform or industry-wide, making them prime targets/opportunities for government intervention. Law enforcement requests for data related to crime are also increasing since most crime now includes some kind of digital footprint. What does your company say to and about law enforcement before, during, and after an engagement? How does your account of an incident compare to law enforcement’s? Should they align or should they be intentionally different? Spoiler: it depends.
Marketing: A lot of security and privacy-related FTC investigations start with a misleading marketing statement or promise on a company website. If you said something in the past that is now clearly not true because of a publicized incident, that’s tasty bait for regulators, including the FTC….and increasingly the SEC, not to mention plaintiff attorneys. If your company hires a creative agency to create your website, get a security subject matter expert to write or review all the copy.
Social Media: Often the front line of customer and public concerns about security issues, social media comments are an unfortunate way to realize your security communications are not aligned across the organization. If you must use prepared responses to scale your ability to address concerns, then social media teams need to be empowered with timely, updated, and technically accurate information that they can share publicly. You might not know if the online persona you’re talking to is a security expert or not, but someone watching certainly is – and as it turns out, a lot of security professionals love to point out anytime something wrong is said on the internet, especially by brands–and especially by their overworked, underpaid social media team members because infosec has no idea how these organizations operate internally.
Customer Support: Working with customer support is about more than having prepared statements when a serious incident occurs or notifying customers if they’re affected; it’s about educating customers about what you’re doing to protect them in advance of an issue as well as demonstrating your ability to respond and recover quickly. It’s also about following through on promises of transparency and positioning your brand as a helpful resource whenever security questions arise. It’s also about helping to drive down the volume and cost of support tickets that reference security issues, especially those where you’ve made strong investments. Additionally, working with these teams gives you good insight into what kind of security concerns are top-of-mind for your customers, so you can potentially preempt them with proactive communications – and accurately predict which type of security incidents will have the greatest impact on customer trust.
Community Managers (e.g. Discord servers and Slack channels): Not every company has these teams, but we work with a lot of developer-first companies where user communities are even bigger than their customer base and have an oversized impact on how customers and beat reporters perceive the organization’s security posture. Similar to bug bounty programs, this is a public-facing organization with a lot of potential to help or hurt a company’s credibility on security issues, and it’s often overlooked by corporate communications teams.
Legal: Their job (and yours!) is infinitely harder if they don’t have a working relationship and workflow with the security team. Fearful lawyers write apathetic, robotic statements that hurt brand sentiment and customer trust. I’ve seen amazing relationships flourish between security and legal teams, leading to public statements and security reputations the company deserves to be proud of. And if you, as a security communications professional, want to be able to share helpful details about a security incident or proactively (& accurately) discuss your company’s commitment to security, it’s in your best interest to ensure a strong partnership between security and legal. CISOs should also prioritize nurturing this relationship, so working together as allies to bring your legal partners along is also a great way to strengthen your relationship with security leadership
Sales: Sales get a bad rap (usually for good reason), but they’re often operating in an information vacuum that commonly exists between marketing materials and a successful proof of concept. Even if they know the product and know the prospect well, they’re usually not subject matter experts in security – this is one reason why sales engineers became so popular at tech vendors over the past several years. It’s in everyone’s best interest to remove security concerns as a reason for prospects not to buy. If you work with sales to identify the most common and most difficult questions they get about security, you can empower them with credible resources to share during sales conversations and a path for how to address concerns they didn’t anticipate. Moreover, if there are questions that make you squeamish for sales to answer directly, work with the appropriate security colleagues to escalate these issues to business leaders to get resolutions prioritized. Otherwise, these weaknesses will come back to haunt you at the worst time.
Product: Not all security incidents involve a breach or intrusion; sometimes they’re product design, policy, or UX decisions that spark a backlash among important stakeholder groups. They require significant resources to mitigate and almost always have a significant impact on brand trust. For example, collecting phone numbers for 2FA and then using that information for targeted advertising despite years of public promises that you weren’t. Product teams have tremendous influence over brand trust and are an important ally in communicating your security commitments and competency. Making security the easy path includes effective communication within the product experience.
HR: If your internal/employee communications function isn’t part of corporate communications, it could be under HR, making them a key partner during incident communications and proactive employee engagements like training and workshops. By pooling resources, you can create greater impact together.
Recruiting: If you’re not yet aware of how your incident history impacts hiring potential or how uninformed recruiters impact your ability to hire security talent, check out this previous post from a senior technical recruiter who hired security teams at Uber, Paypal, Lime, and more.
“Often recruiters aren’t in the loop or armed with the right messaging and talking points about a company’s security posture – or if there has been a security incident or other reputation-affecting situation. Not all tech candidates will ask about these things, but security candidates often want to know.
I want to be as honest and transparent as I can be with potential hires, so having accurate information from my security communications colleagues makes a big difference. Some companies are better at this than others and that impacts how they’re perceived by candidates even before they start interviewing.”
Public Policy: Waiting until you get a letter from Congress is the wrong approach to security communications with the government. Coaching public policy colleagues in the areas of security where your organization is not only strong but also has a strong point of view is important to ensure your interests are heard at the appropriate levels of policy-making at the local, state, and federal levels (or applicable structures outside the U.S). Be ready to respond at a moment’s notice to basic as well as controversial questions about your security programs and technical controls. This is an area where industry allies can be really helpful and you can help public policy colleagues identify the appropriate folks to bring to the table in government discussions.
Engineering & Data Science: Usually these are different teams, but we engage with them for many of the same reasons — they love to talk about their work, and they’re not always aware of how various project names, descriptions, and design decisions interact with stakeholder expectations on security issues.
These are some of the most common teams we work with, but the most important thing is that no matter where you sit in an organization, you find all the other people working on security communications across the company and create a cross-functional working group and tie your collaboration directly to the company’s core business objectives.
By working together, you have more strategic alignment, more information, more resources, more justification, and ultimately, more impact. If you find yourself trying to scale your subject matter expertise and governance across cross-functional partners, let’s talk! There are proven strategies for empowering other teams with resources they can use on their own while setting guidelines and triggers to ensure direct oversight when needed.
To learn more about how Discernible’s security communications strategies can create and expand influential relationships for your security team, contact us.